Issues regarding cybersecurity have been the topic of a lot of news lately. Recently, Sophos, A global cybersecurity company, released new information regarding the Tor2miner cryptominer that shows how the miner variant can evade detection, became more aggressively invasive, and more persistent.
Tor2Mine is a Monero-miner that has been active for the past two years. Sophos’ research explains new variants that include a Powershell script that can attempt to disable malware protection, execute miner payload, and gain windows administrator credentials. The next step will depend on whether the stolen windows credentials of the attacker can gain administrative privileges. All variants analyzed have the same process.
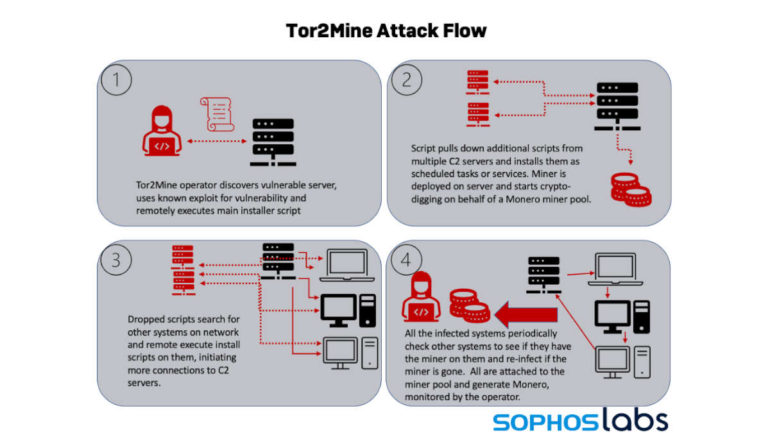
In the occasion that the attacker does not gain admin privileges, Tor2Mine can still execute the miner remotely and filelessly by running commands that work as scheduled tasks. By doing this, the miner software is stored remotely rather than on the infected machine.
All these variants attempt to shut down anti-malware protection and install a similar miner code. In all cases, the miner will continuously infect systems in the same network unless it is stopped by malware protection or is completely deleted from the said network.
“The presence of miners, like Tor2Mine, in a network is almost always a harbinger of other, potentially more dangerous intrusions. However, Tor2Mine is much more aggressive than other miners. Once it has established a foothold on a network, it is difficult to root out without the assistance of endpoint protection software and other anti-malware measures. Because it spreads laterally away from the initial point of compromise, it can’t be eliminated just by patching and cleaning one system. The miner will continually attempt to re-infect other systems on the network, even after the command-and-control server for the miner has been blocked or goes offline. As cryptocurrencies continue to increase in value and support the ever-growing ransomware and cyberextortion landscape, we may well see more, and more aggressive, variants of other cryptominers emerge.”
Sean Gallagher, Senior Threat Researcher at Sophos
Researchers at Sophos have discovered scripts designed to kill off a variety of processes and tasks. Most of them are related to cybercrimes that include competing cryptominers and clipper malware that can steal cryptocurrency wallet addresses.
“Miners are a low-risk way for cybercriminals to turn a vulnerability into digital cash, with the greatest risk to their cash flow being competing miners discovering the same vulnerable servers,” Gallagher added.
Here are some steps that Sophos recommends to help organizations protect their networks and endpoints against cryptominers like Tor2Mine:
- Patch software vulnerabilities quickly on internet-facing systems, such as web applications, VPN services, and email servers, as this will make them far less likely to fall victim to cryptominers
- Install anti-malware products – miners are usually easily detected by such technologies – particularly those that leverage Windows’ Anti-Malware Software Interface (AMSI) to spot scripts intended to shut down malware protection
- Monitor for unusually heavy use of processing power, reduced computer performance, and higher than expected electricity bills, as any of these, can indicate the presence of cryptominers on the network
Lastly, Sophos detects Tor2Mine as the MineJob family (MineJob-A through E) and detects the script behaviors of every known variant.
If you want to know more about the Tor2Miner cryptominer, Click here.
Started his freelancing adventure in 2018 and began doing freelance Audio Engineering work and then started freelance writing a few years later.
Currently he writes for Gadget Pilipinas and Grit.PH.
He is also a musician, foody, gamer, and PC enthusiast.







