In light of the recent emergence of the WannCry ransomware, computer security firm Symantec has given an insight as to what this threat is, and what damage is it capable of doing.
So what exactly happened?
Last May 12, 2017, a new variant of the Ransom.CryptXXX family of ransomware started to infect a large number of machines, leaving a huge impact on organizations, particularly in Europe.
What is the WannaCry ransomware?
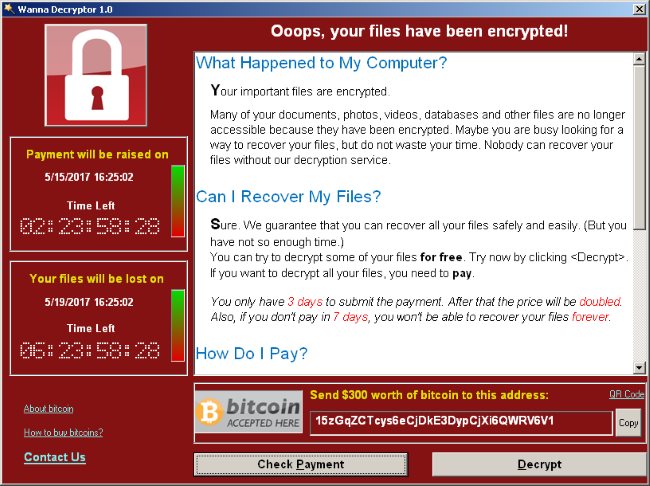
The WannaCry ransomware encrypts files and asks the user to pay USD300 worth of bitcoins as ransom, so that he/she can get the software to decrypt the files.
There’s also a note telling the user that the payment amount will be doubled after 3 days. If payment is not made after 7 days, the encrypted files will then be deleted.
The ransom note is located on a text file named !Please Read Me!.txt
Which file types does WannaCry encrypt?
- 123
- .3dm
- .3ds
- .3g2
- .3gp
- .602
- .7z
- .ARC
- .PAQ
- .accdb
- .aes
- .ai
- .asc
- .asf
- .asm
- .asp
- .avi
- .backup
- .bak
- .bat
- .bmp
- .brd
- .bz2
- .cgm
- .class
- .cmd
- .cpp
- .crt
- .cs
- .csr
- .csv
- .db
- .dbf
- .dch
- .der
- .dif
- .dip
- .djvu
- .doc
- .docb
- .docm
- .docx
- .dot
- .dotm
- .dotx
- .dwg
- .edb
- .eml
- .fla
- .flv
- .frm
- .gif
- .gpg
- .gz
- .hwp
- .ibd
- .iso
- .jar
- .java
- .jpeg
- .jpg
- .js
- .jsp
- .key
- .lay
- .lay6
- .ldf
- .m3u
- .m4u
- .max
- .mdb
- .mdf
- .mid
- .mkv
- .mml
- .mov
- .mp3
- .mp4
- .mpeg
- .mpg
- .msg
- .myd
- .myi
- .nef
- .odb
- .odg
- .odp
- .ods
- .odt
- .onetoc2
- .ost
- .otg
- .otp
- .ots
- .ott
- .p12
- .pas
- .pem
- .pfx
- .php
- .pl
- .png
- .pot
- .potm
- .potx
- .ppam
- .pps
- .ppsm
- .ppsx
- .ppt
- .pptm
- .pptx
- .ps1
- .psd
- .pst
- .rar
- .raw
- .rb
- .rtf
- .sch
- .sh
- .sldm
- .sldx
- .slk
- .sln
- .snt
- .sql
- .sqlite3
- .sqlitedb
- .stc
- .std
- .sti
- .stw
- .suo
- .svg
- .swf
- .sxc
- .sxd
- .sxi
- .sxm
- .sxw
- .tar
- .tbk
- .tgz
- .tif
- .tiff
- .txt
- .uop
- .uot
- .vb
- .vbs
- .vcd
- .vdi
- .vmdk
- .vmx
- .vob
- .vsd
- .vsdx
- .wav
- .wb2
- .wk1
- .wks
- .wma
- .wmv
- .xlc
- .xlm
- .xls
- .xlsb
- .xlsm
- .xlsx
- .xlt
- .xltm
- .xltx
- .xlw
- .zip
The ransomware appends .WCRY at the end of the filename. It also propagates to other computers by taking advantage of a known SMB remote code execution vulnerability in computers running on Windows (MS17-010).
Am I protected against this particular threat?
Symantec and Norton users are kept safe from WannaCry using a combination of technologies.
Antivirus
Customers should run LiveUpdate and ensure that they have the 20170512.009 definition version or later.
SONAR protection
- SONAR behavior detection technology is also able to detect Wannacry variants.
Network based protection
Symantec has proven itself highly effective in proactively blocking attempts to exploit the MS17-010 vulnerability. It also has the following IPS protection in place:
The following IPS signature also blocks activity related to Ransom.Wannacry:
Organizations should also ensure that they are running on the latest Windows security updates installed, in particular MS17-010 to prevent spreading.
Who is impacted?
A number of organizations globally have been affected, with the majority being in Europe.
Is this a targeted attack?
No, this is not perceived as a targeted attack at this time. Ransomware campaigns are usually indiscriminate.
Why is it causing so many problems for organizations?
WannaCry has the ability to propagate within corporate networks without user intervention by exploiting a vulnerability in Windows. Computers which do not have the latest security updates applied are at risk of infection.
Can I recover the encrypted files?
Decryption is not yet available, but Symantec is investigating. In any case, Symantec does not recommend paying the ransom. Encrypted files should be restored from back-ups whenever possible.
What are best practices for protecting against ransomware?
- Always keep your security software up to date.
- Keep your operating system and other software updated.
- Email is one of the main infection methods. Watch out for unexpected emails especially if they contain links and/or attachments.
- Be extremely wary of any Microsoft Office email attachment that asks you to enable macros to view its content. Unless you are sure that this is a genuine email from a trusted source, do not enable macros and immediately delete the email.
- Backing up your data is the most effective way of combating ransomware infection. Attackers have leverage over their victims by encrypting valuable files and leaving them inaccessible. If the victim has backup copies, they can restore the files when the infection has been cleaned up. However, organizations should ensure that back-ups are protected or stored off-line so that attackers can’t delete them.
- Using cloud services could help reduce the risk of ransomware infection, since many retain previous versions of files, allowing you to “roll back” to the unencrypted form.
Photo: wikimedia
Emman has been writing technical and feature articles since 2010. Prior to this, he became one of the instructors at Asia Pacific College in 2008, and eventually landed a job as Business Analyst and Technical Writer at Integrated Open Source Solutions for almost 3 years.